Twenty years ago, the world was a very different place: the invention of Gmail was still two years out, we were five years prior to the advent of the iPhone, and if you asked someone to ‘Zoom’ into a meeting, you’d likely have been met with a strange look.
For most folks at this time, the concept of cybersecurity norms was somewhat foreign – and even further from focus was the policy governing it.
Nowadays, cybersecurity policy has increased in importance and prominence, frequently at the center of attention in the wake of threats like the SolarWinds attack and the Log4J exposure. These headline-stealing events have served as a sharp reminder that as our technology advances, so must our security policies.
The Cybersecurity Landscape
Cybersecurity has grown into a global, almost omnipresent issue with predictions showing cumulative spending could be as high as $1.75 trillion by 2025.1
Whether you’re talking about a continent or a company, one thing’s for sure: various protocols and requirements govern the cybersecurity landscape.
Out of this patchwork, industry players have proactively developed security policy that foster innovation and enhance consumer safety and trust. By safeguarding digital assets, monitoring data leaks and authenticating devices, industry players have had a leading role in establishing robust policies to help ward off online threats in a multitude of ways.
Learn what organizations globally are doing to proactively transition security as they innovate at the edge with our 2022 Cybersecurity Insights Report.
One example of this is the widespread adoption of what’s commonly referred to as two-factor authentication. Yes – you know it well – the pesky pin number that’s sent to our phones even when we got our password right!
Another example is what is called “zero trust.” The concept was introduced in the late 2000s by John Kindervag at Forrester Research when he realized that viewing anything inside the perimeter firewall as “trusted” can lead to risk from an attacker who gets passed that firewall. With zero trust, there is continuous risk-based evaluation and authentication for each system or interface as users must continuously re-authenticate when they access different systems within a firm.
- Zero trust has become a foundational concept in developing modern security architectures and was specifically required for federal agencies in President Biden’s 2021 Executive Order.
- Zero trust is a framework to guide security policy, it is not a product. Each organization will implement zero trust differently – it comes down to business decisions regarding risk appetite.
Our Cybersecurity Protocols and Goals
This idea of standard setting – which requires constant innovation, investment and modification to meet ever-evolving security circumstances – can be daunting, especially for new entrants to the market.
But at AT&T, we have been developing and updating our own cybersecurity policies for years. AT&T security requirements serve as a guide and a reference point to conducting business in a secure environment and protecting AT&T information resources.
- Our security requirements are a comprehensive set of security control standards based, in part, on leading industry standards such as ISO/IEC 27001:2013. And it’s continually reevaluated and modified to be best in class.
- Its rigor is such that it preemptively aligned with laws and standards such as the National Institute of Standards & Technology (NIST) Cybersecurity Framework as well as the E.U.’s General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA).
Nonetheless, we are vigilant of our own limitations and recognize that continuous collaboration in this space is essential – whether that’s by engaging with stakeholders or convening open exchanges with the cyber intelligence community.
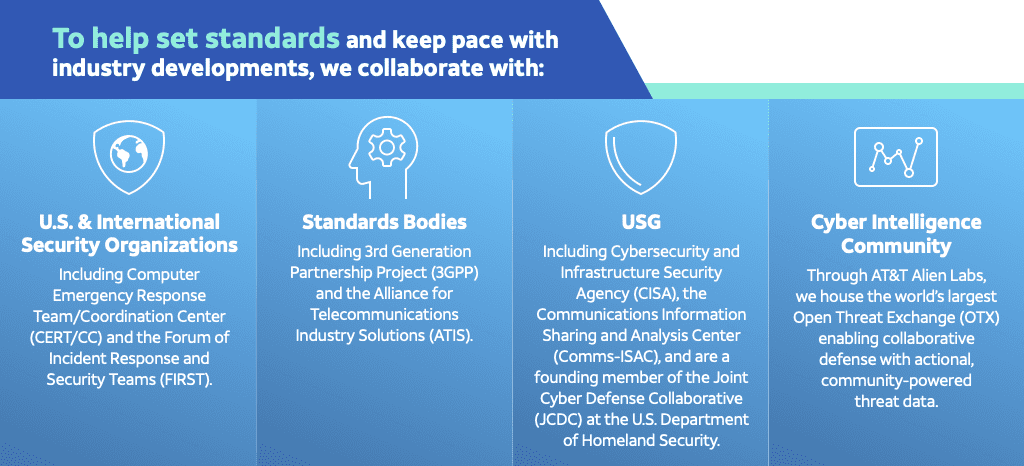
These best practices are a small window into the vast measures we take across the globe to keep such a complex piece of infrastructure safe and secure for daily users. So, when AT&T expands its networks – whether it be to the most rural farms or the most densely populated metro areas – those networks will be backed by a legacy of existing and proven cybersecurity practices.
Thoughtful Public Policies Can Help Keep Americans Secure
To meet the moment, there are several different policy approaches being proposed federally to establish a holistic and secure cyber landscape in the U.S.
- The Biden Administration is expected to release a National Cybersecurity Strategy in the near future, the Securities and Exchange Commission has proposed rules on reporting requirements and the Department of Homeland Security is currently conducting a rulemaking to implement cyber incident reporting legislation signed last March.
- Additionally, CISA developed baseline cybersecurity performance goals for critical infrastructure.
- In May 2021, the Biden Administration’s executive order urged the federal government to develop plans to implement zero trust architecture.
When creating and evaluating public policies aimed at fortifying our cyber defenses, it is important to strike the right balance between raising the bar for security while at the same time ensuring room for innovation. It’s critical that incident reporting rules are practical and do not create an undue burden on companies diverting their attention away from the day-to-day practice of cybersecurity or from responding to an incident.
To ensure harmonization, performance goals or security baselines should stem from industry best practices and standards like the NIST Cybersecurity Framework. To the extent that there are unique issues to a given sector of critical infrastructure, those standards can be augmented to address those specific concerns.
As the vast majority of critical infrastructure in the U.S. is owned by the private sector – collaboration between government and the private sector is critical to the success of these programs. We have been encouraged by the Administration’s outreach to industry to date. In the future, continued partnership and long-term engagement is key.
Cybersecurity will also require collective action from all players in the digital ecosystem – from equipment manufacturers, network operators, tech platforms, government institutions and more. We will have to work together to protect our companies, customers and friends. Due to its sheer size and reach, the internet cannot be the domain or responsibility of any one entity.
The Bottom Line
An effective cybersecurity landscape benefits us all – from the largest corporations and government agencies to the countless small businesses that make up the backbone of America’s economy.
As we discussed in the second cybersecurity blog of this series, cybersecurity policies are impactful across all industries that utilize technology, including:
- Healthcare: First responders need secure networks to save lives.
- Finance: This industry relies heavily on network security to keep America’s economic engine strong.
- Manufacturing: Manufacturers need reliable networks to avoid supply chain disruptions.
Check out our 2022 industry vertical reports on energy and utilities, healthcare and state and local government and education (SLED).
It’s imperative that we use the historic infrastructure investment to expand connectivity while keeping cybersecurity in mind. We believe that policymakers and key industry players alike will see the opportunity at hand to use these funds to bolster secure connections. Recognizing how key enterprises have paved the way for modern cybersecurity solutions, we can learn from and build upon the approaches that have worked for businesses and industries thus far. The result?
Our future policies will be that much stronger.
1 2022 Cybersecurity Spending Trends | Dataprise (March 11, 2022)





